Antikor - ZTSA (Zero Trust Service Access)
General Introduction
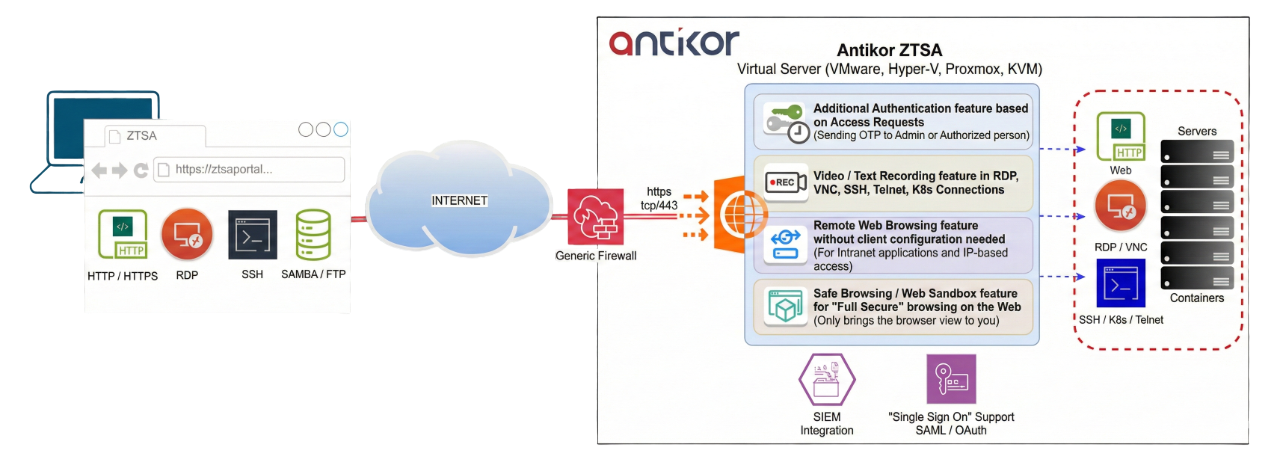
Antikor ZTSA (Zero Trust Service Access) software is an agentless, browser-based ZTSA platform operating over the SSL port, designed as a next-generation Privileged Access Management (PAM) solution. It does not provide users with direct access to services such as RDP, SSH, VNC, Telnet, Kubernetes Console, Remote Web Browsing, SafeBrowsing / Web Sandbox, or File Browser. Instead, it delivers highly secure, low-risk connections by transmitting only screen output and user interactions, thereby preventing direct exposure of internal systems and minimizing attack surfaces.
What is Zero Trust Service Access (ZTSA)?
ZTSA (Zero Trust Service Access) is an access security model based on the “Zero Trust” approach. In this model, no user or device on the network is trusted by default. Every access request is permitted only after passing through authentication and authorization filters. In short, it operates on the logic of “Never trust, always verify.”
Antikor ZTSA ensures that users and devices connect only to the applications and services they need via a secure tunnel, rather than the entire network. This provides:
- Minimizing the Attack Surface: Unlike VPNs that allow direct server access, clients cannot connect to the server directly.
- Protocol Adaptation: Instead of accessing services like RDP or SSH directly, users connect to the Antikor ZTSA portal via HTTPS. Antikor ZTSA acts as a protocol adapter.
- Prevention of Exploits: Service scanning and exploit attempts common over VPN connections are completely eliminated.
- Prevention of Lateral Movement: Blocks lateral movement and ransomware risks.
- Full Visibility: Provides complete visibility by logging all access requests in detail.
- Broad Service Support: Unlike typical PAM products, it works agentless and supports RDP, SSH, K8s, Telnet, VNC, Web applications, and File Exchange (FTP, SFTP/SCP, SMB/CIFS, WebDAV, S3, Google Drive).
- Collaboration Features: Includes capabilities such as joining active sessions live and co-managing sessions.
- Secure Access to Internal Apps: Intranet applications and monitoring web interfaces can be securely exposed.
- ShareMyScreen: Unlike solutions like Anydesk/Teamviewer, our screen-sharing feature keeps traffic on-premise (within the company) instead of the cloud for secure remote support.
- Advanced Authentication & Compliance: Strengthens security with MFA, LDAP/Active Directory, RADIUS-Challenge, and SSO. It offers full compliance with corporate auditing standards and legal regulations via Audit Logging and SIEM (CEF, JSON) integrations.
- Easy Deployment: Offered as a Virtual Appliance, allowing for fast and flexible deployment without requiring changes to your existing network topology.
- Scalability: Its container-based architecture allows for dynamic horizontal scaling based on demand.
Product Architecture
It is offered to the market as a Virtual Appliance (VMWare ESXi / vSphere, Microsoft Hyper-V, Proxmox, KVM-based Hypervisors) and is fully compatible with all Firewalls. It presents a completely new approach to remote access for internal systems. Unlike traditional VPNs, it does not allow users to access the server directly, thereby minimizing security vulnerabilities.
 {width=900 height=328}
{width=900 height=328}
Regulations Regarding the Use of Antikor ZTSA
Antikor ZTSA integrally meets the requirements specified in the following regulations:
- “Maintenance of connection logs” (ZTSA Access Log)
- and more importantly, “Creation of user activity audit trails” (ZTSA Video and Text Session Recordings)
Supported Services
- Configuration-free, Agentless Web Proxy (HTTP / HTTPS)
- RDP (Remote Desktop Protocol)
- Secure File Sharing
- Audio, Clipboard, and Printer Sharing
-
Ability to define Initial Program
- SSH - Secure Shell
-
Password & Public Key Authentication
- Screen Sharing with Remote Control Capability
- VNC (Virtual Network Computing)
- K8s & Kubernetes Console
- Telnet
- Remote Web Browsing (Browse the internet remotely and securely)
- Safebrowsing / Web Sandbox (Open the browser in an isolated environment, examine without risk)
- Screen Sharing (Remote Control Access via Link)
- Proxy Access via Agent (Windows, Mac OS, Linux supported)
- File Access via File Browser
- FTP - File Transfer Protocol
- SFTP - SSH File Transfer Protocol
- SMB/CIFS - Server Message Block (Common Internet File System)
- WebDAV - Web Distributed Authoring and Versioning
- SCP - Secure Copy Protocol
- Google Drive integration
-
AWS S3 compatible Storages, (MinIO)
- Wake on LAN support
- Joining Active Sessions: Screen Monitoring / Management (Multiple participants)
Access Control Features
- Access Control based on Service, Group, User, and Role
- Access permission expiration date control
- Providing access permission on specific days
- Providing access permission during specific hours
- Connection Security with Additional Approval (Sponsored)
- Ensuring the connection is established only after an OTP is sent to and approved by an authorized user.
Security Features
- Encrypted Credentials Storage
- File Exchange Security
- ACL-based, Antivirus Scanning Support
-
Optional Sandbox API Integration
- Client - RDP drive share isolation
- Session Recording for RDP and VNC
- Screen Video recording
-
Text Screen Recording for SSH, Telnet, K8s
- Encrypted Credentials Storage
- Session Start and End Logs
Integration Features
- SIEM / Syslog Integration
-
CEF, JSON Formats
- Audit Log Integration
- External Sandbox Integration
- External Antivirus Integration
Authentication Methods
- Local User
- Single Sign-On
- SAML 2.0
- OAuth 2.0
-
OpenID Connect
- RADIUS - MFA and Challenge Supported
- LDAP / Active Directory
- MFA - Multi-Factor Authentication (OTP, TOTP)
Management Interface Features
- HTML5 Responsive Web Interface
- Event Notification Infrastructure
-
SMS, Email, Browser Notification, Webhook
- Access Logging
- Personalized Favorite Services
- Permission-based Configuration Override Support
- Light / Dark Mode Support
- Grid / List View Support
- Service Grouping Support
- Access Request Management Module
- Quick Search Module
- Reporting Module
- Permission Management
Scalability
Antikor ZTSA is designed in compatibility with modern container orchestration architectures such as Kubernetes and Docker Swarm. In this way, the system can scale horizontally automatically even under heavy user load.
Depending on the resources provided by the infrastructure, the system can manage thousands of people simultaneously and connect them to services without interruption. Since it can work integrated with existing virtualization, Kubernetes, or Docker Swarm infrastructures, organizations do not need to make additional hardware investments.
For High Availability, both the authentication services and the services provided to users are managed with Load Balancing and failover mechanisms. Service continuity is guaranteed through this structure.
Highlighted Advantages
- High Security & Zero Trust Architecture: Users are not given direct access to systems. Only screen images and input interactions are carried, minimizing the attack surface.
- Browser-based Access & Installation-free Use: No software or agent installation is required on the user side. Instant access to RDP, SSH, VNC, Telnet, and more is provided using only a web browser.
- Secure VPN Alternative: Antikor ZTSA is a more secure and easier-to-manage alternative compared to VPNs. Alternatively, it can connect via its own Agent if desired.
- Advanced Authentication & SSO Support: Integrates with existing corporate user accounts: Secure and one-click login with SAML 2.0, OAuth 2.0, OpenID Connect.
- Resource-Based Authorization: Each user can only see and access the systems they are authorized for. Access control is easily managed from the central panel.
- Recording and Auditing Mechanism: All sessions can be monitored and audited. Logins/logouts, access records, and system behaviors can be analyzed retrospectively.
- Fast Installation, Easy Management: You can deploy the system in minutes and manage all access centrally. Great operational convenience for IT teams.
- Flexible Integration: Easily integrates with different data centers, identity providers, and security solutions. No need to change your existing infrastructure.
- Ideal for Remote Work: Offers secure, limited, and traceable access to your personnel working outside the company. Secures location-independent working.
Example Usage Scenario
Secure, Installation-free, and Auditable Access from Outside the Campus
Scenario: In a university or affiliated hospital; applications such as Web of Science, Scopus, YÖK Thesis, and EBYS are only accessible from within the campus. However, needs extend beyond the campus.
For Academicians — Installation-free and Secure Access
- Secure remote access to academic resources (TRDizin, Scopus, etc.)
- One-click login with corporate SSO
- No additional password or installation required
- IT support decreases, user experience increases
RDP Access Given to External Companies
- External support access is provided without VPN
- Access is granted only to the relevant system
- Browser-based, secure, and traceable
SSH and Web Access to Network Devices (Switch, AP, Firewall)
- Access definition only for authorized devices
- Access to SSH and Web interfaces via browser
- Recorded, secure, and restricted connection
- No direct connection to the device — attack surface is zeroed
Antikor ZTSA System Educational Institution Models and Product Details
| No | Product Code | Product Name | Link |
|---|---|---|---|
| 1 | EPA-ZTSA-EDU-500 | Antikor ZTSA (Zero Trust Service Access) System | Datasheet |
| 2 | EPA-ZTSA-EDU-1K | Antikor ZTSA (Zero Trust Service Access) System | Datasheet |
| 3 | EPA-ZTSA-EDU-2K | Antikor ZTSA (Zero Trust Service Access) System | Datasheet |
| 4 | EPA-ZTSA-EDU-5K | Antikor ZTSA (Zero Trust Service Access) System | Datasheet |
| 5 | EPA-ZTSA-EDU-10K | Antikor ZTSA (Zero Trust Service Access) System | Datasheet |
Antikor ZTSA System Commercial Models and Product Details
| No | Product Code | Product Name | Link |
|---|---|---|---|
| 1 | EPA-ZTSA-PRO-100 | Antikor ZTSA (Zero Trust Service Access) System | Datasheet |
| 2 | EPA-ZTSA-PRO-250 | Antikor ZTSA (Zero Trust Service Access) System | Datasheet |
| 3 | EPA-ZTSA-PRO-500 | Antikor ZTSA (Zero Trust Service Access) System | Datasheet |
| 4 | EPA-ZTSA-PRO-1K | Antikor ZTSA (Zero Trust Service Access) System | Datasheet |
| 5 | EPA-ZTSA-PRO-3K | Antikor ZTSA (Zero Trust Service Access) System | Datasheet |
| 6 | EPA-ZTSA-PRO-6K | Antikor ZTSA (Zero Trust Service Access) System | Datasheet |
| 7 | EPA-ZTSA-PRO-10K | Antikor ZTSA (Zero Trust Service Access) System | Datasheet |